Definitions
Computer Network
A network is two or more computers - or other electronic devices - that are connected together for the purpose of communication. It allows for the sharing of resources such as printers etc.
PAN (Personal Area Network)
A PAN is a network that is spread over a very small area. It often covers no more than a few metres and is used to connect personal devices such as a smartphone and wireless headphones or a laptop. Makes use of limited Wi-Fi or Bluetooth.
LAN (Local Area Network)
A LAN is a network that connects computers within a limited geographical area such as a residence, school, or office building. Usually controlled/managed by one person/organisation.
WAN (Wide Area Network)
A WAN is a network that extends over a large geographic area, often countrywide or worldwide. Usually under collective or distributed ownership.
Router
A device that forwards data packets between computer networks, determines the best path for data.
Swicthes
Network devices that record which computers are connected to which ports. When traffic is received, the switch forwards the traffic to its intended recipient only. This improves network performance by cutting down on unnecessary transmissions from older style networks.
Network Protocol
A set of rules or procedures that allow devices/networks to communicate.
Node
Any device connected to a network.
MAC Address
Each device connected to the network has a (unique) address.
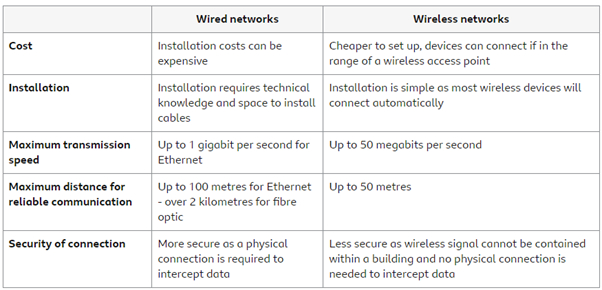
Wired Networks - The use of physical wiring to connect devices. Often used for office networks or for devices that are unlikely to move as the cables limit the ability to move away from the connection point.
Wireless Networks - Use radio waves to carry signals. Limited in range (usually up to 50 metres and are subject to interference). They are ideal for mobile devices as the device can connect to a network as long as it is in range of the Wireless Access Point (WAP).
Bus Topology -
In a bus topology, all nodes in the network are connected directly to the central cable (backbone) that runs up and down the network. Data is sent up and down the backbone until it reaches the correct node.
Advantages -
- It is easy to connect nodes to the network
- Less cabling is needed compared to a star topology, making it cheaper to install
Disadvantages -
- If the backbone is broken the whole network fails
- Having one backbone increases the chances of data collision
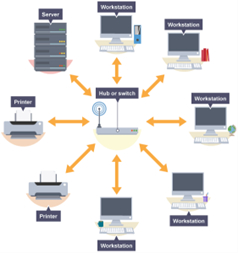
Star Topology -
All nodes indirectly connect to each other through one or more switches. The switch acts as a central point through which all communications are passed.
Advantages -
- Each node is connected separately, so if one node or its link fails, it does not affect any other node
- New nodes can be added to the network by simply connecting them to the switch
- Tend to have higher performance as a message is passed on to its intended node only
Disadvantages -
- If the switch fails the whole network fails
- Requires a lot of cabling so can be expensive
Protocols and standards are crucial for communication within networks. They ensure that data is transmitted correctly across networks with different architectures and technologies. Important protocols include:
- TCP/IP: This set of protocols governs the connection of computer systems to the Internet.
- Ethernet: A family of related protocols rather than a single protocol.
- HTTP (Hypertext Transfer Protocol): Provides a way for users to interact with web resources. Transmits messages between client and server using hypertext.
- HTTPS (Hypertext Transfer Protocol Secure): Same as HTTP but in addition uses an encryption protocol to ensure communications are secure.
- FTP (File Transfer Protocol): Allows secure transfer of files between client and server. Files are uploaded to and downloaded from the server using FTP.
- SMTP (Simple Mail Transfer Protocol): Enables users to send (and receive) email messages. Initiates sessions between user and mail server. Server then forwards messages. Uses a process called ‘store and forward’ to store messages and forward as necessary. The server decides which server to send the message to and the inbox provider then downloads the message and places it in the recipient’s inbox. Often used in conjunction with IMAP. (Used for email).
- IMAP (Internet Message Access Protocol): Stores email messages on an ISPs (internet service provider) server but allows user to manipulate messages as though on a local device. Local devices access the ISP server to access the messages. IMAP works with desktop clients and webmail clients. Allows simultaneous logins from different devices to one account. (Used for email).
- TCP (Transmission Control Protocol): Connects network devices to the Internet. It defines how applications can create channels of communication across a network. It manages how a message is assembled into smaller packets before transmission and reassembles packets in the correct order at destination.
- UDP (User Datagram Protocol): Communications protocol that establishes low latency and loss-tolerating connections between applications. Enables the transfer of data before an agreement is provided by the receiving party. This speeds up transfers. Can start transferring data before agreement is received from receiving party.
- IP (Internet Protocol): Relays data across network boundaries. It defines how to address and route each packet to make sure it reaches the right destination.
Why do we use layers?
It breaks up the sending of messages into separate components and activities. Each component handles a different part of the communication. Layering enables standards to be put in place and simply adapted as new hardware and software is developed.
Application Layer
- Where network applications operate such as web browser, emails etc.
- Protocols in this layer - HTTP, HTTPS, SMTP, IMAP, FTP
Transport Layer
- Sets up the communication between the two hosts, using protocols such as TCP and UDP
- Splits the data into packets
- Protocols in this layer - TCP, UDP
Internet Layer
- Adds IP addresses to the packets of the sender and the receiver
- Routes the packets across the network
- Protocols in this layer - IP
Link Layer
- Where network hardware operates (e.g. network interface card)
- Where operating device drivers operate
With the increasing amount of data being shared across networks, security has become a major concern. Key security measures and concepts include:
Firewalls: A firewall is software that blocks unexpected connections coming into or out of a network. Most operating systems include a firewall as a piece of software, but firewalls can also be hardware devices that sit alongside or as part of the router.
Firewalls use ports which only allow specific data into and out of networks. The network manager is able to open or close the ports depending on the type of traffic they want to use for the network. By keeping more ports closed on a firewall, less internet traffic can come through, making the network more secure.
Encryption: Encoding of data so that it can no longer be easily understood. Encryption requires the use of a key. The key is secret as to how the message has been disguised. Unencrypted messages are referred to as plaintext messages and encrypted messages are known as ciphertext.
Authentication: The process of a user confirming that they are who they say they are on a computer system. In a network, this is often done through inputting a username and password. For networks that require high levels of security, this may include other factors.
MAC address filtering:
Because a device's media access control (MAC) address is unique to the device, the network manager can create a more secure network by using this address to limit the devices on the network.
They have two options to do this:
- A whitelist - only the device addresses on the list are allowed to access the network. This is more secure, but creates extra work for the network manager as they must add data every time a new device needs to join the network.
- A blacklist - devices on the list are banned from the network. This is less secure than a whitelist, but is easier to maintain.